Welcome to our guide to integration security for B2B SaaS products!
This guide is for product leaders, engineering leaders, and security officers at B2B SaaS companies that provide integrations connecting their products to the other products their customers use.
You'll find it helpful whether you're preparing to build your product's first integrations, reexamining your existing integration strategy through a security lens, or considering implementing an embedded integration platform (embedded iPaaS) to accelerate your integration roadmap.
Product integrations are challenging to get right because of many complexities. Undoubtedly, security is one of the most inherently difficult – and most important.
Many of these security principles may be familiar to you from a general software or SaaS context – after all, integrations are software. However, it is still too common for integrations to not receive the same care and focus as your primary SaaS product. We believe that integrations should be first-class citizens within your product portfolio.
Every integration is different, and so are its security needs. In a guide like this, we can't get into much detail on specific integrations, but we hope that this overview helps you and your team ask the right security questions as you plan and build your integrations.
As the team behind the industry-leading embedded integration platform (embedded iPaaS), we at Prismatic are excited to share this with you.
In this guide, you will learn:
- The importance of security for integrations
- Common integration security threats and their impacts
- Best practices you can implement to mitigate security risks
Section 1: Overview of integration security
What is an integration?
An integration is the code allowing one system to transfer data to or from another. Most integrations work with an application programming interface (API) on at least one end of the integration. APIs are crucial tools in software development, allowing users and applications to interact with software without understanding its inner workings.
APIs have different patterns, such as REST, RPC, GraphQL, Polling, Web Sockets, and webhooks. API integrations power processes throughout most businesses to keep data in sync, enhance productivity, and drive revenue.
Since most software development now happens in a SaaS context, an increasing number of integrations are SaaS integrations, connecting SaaS apps to other SaaS apps or connecting SaaS apps to on-premise apps. We'll use the terms SaaS integrations and integrations interchangeably throughout this guide.
What is integration security?
Integration security refers to the measures and practices that ensure the safe exchange of data and the secure operation of interconnected systems in a digital environment. This concept is especially critical when different software applications are linked to work as a cohesive unit. The primary goal of integration security is to protect the integrity, availability, and confidentiality of data as it moves between systems.
Several key elements of integration security are:
- Data integrity and protection: Ensuring that data transferred between systems is protected against unauthorized access, manipulation, and loss. This involves using encryption during data transmission and, often, while data is at rest.
- Authentication and authorization: Verifying that only legitimate users and systems can access and interact with integrated systems. This can involve various authentication mechanisms, such as passwords, tokens, or more sophisticated methods like OAuth.
- Secure APIs: Since most integrations involve APIs, ensuring that these APIs are secure is crucial. This includes implementing rate limiting, logging, and regular security assessments to prevent common vulnerabilities like injections and data breaches.
- Compliance with regulations: Adhering to relevant legal and regulatory requirements such as GDPR, HIPAA, or CCPA, which dictate how data should be handled and protected, particularly personal and sensitive information.
- Error handling and logging: Properly managing how integration errors are handled and logged prevents the leakage of sensitive information through error messages and ensures that operational issues can be traced and rectified efficiently.
- Monitoring and detecting anomalies: Continuously monitoring the integrated systems for any unusual activity that could indicate a security breach or operational malfunction. This involves setting up system alerts and having a response plan in place.
- Network security: Securing the network channels through which the integrated systems communicate. This can include using VPCs and security groups to control network traffic.
Integration security is a complex field that encompasses a range of technologies and strategies to ensure that as systems become more interconnected, they do not become more vulnerable to attacks or operational issues. It is a critical part of any B2B SaaS organization's broader IT security and risk management strategy.
Integrations are critical for the current technological landscape
Integrations play a critical role in the current technological landscape, especially as businesses increasingly rely on an array of cloud-based software applications to operate efficiently.
If you are a product leader, you are well aware of how critical integrations are for your SaaS product. However, if you have a different role where you’re not as familiar with integrations, you may be wondering why we are putting such an emphasis on them. If so, this section is for you.
Here are some of the ways integrations contribute to business practices:
- Enhanced efficiency and automation: Integrations allow different software systems to communicate and share data, automating workflows that would otherwise require manual intervention. This automation speeds up processes and reduces the likelihood of errors, improving overall operational efficiency.
- Improved data accessibility and management: Integrations link systems and ensure that data flows freely across different parts of a business. This connectivity helps organizations maintain up-to-date, consistent, and accurate data across all systems, improving decision-making and data management practices.
- Scalability: As businesses grow, their needs become more complex. Integrations allow for scalability by enabling businesses to add new tools and technologies without disrupting existing systems. This adaptability is crucial for growth and expansion in a fast-paced business environment.
- Enhanced customer experience: Integrations facilitate a smoother, more cohesive user experience by connecting various customer service apps, CRM systems, and marketing tools. This connectivity ensures that customer interactions are consistent and informed across all touchpoints, enhancing customer satisfaction and loyalty.
- Cost reduction: Integrations can significantly reduce costs by eliminating the need for multiple standalone systems and reducing reliance on manual processes. Businesses can lower operational costs and improve the bottom line by streamlining operations and reducing inefficiencies.
- Innovation and competitive advantage: Integrations enable businesses to leverage the best capabilities of each software tool. By integrating cutting-edge technologies and systems, companies can stay ahead of the curve, innovate more effectively, and maintain their competitive edge.
- Compliance and security: With increasing regulatory demands concerning data privacy and security, integrations help ensure that data handling across systems complies with legal and regulatory requirements. Appropriate integrations can help safeguard sensitive information and reduce the risk of data breaches.
Section 2: Understand integration security threats and risks
Integrations are subject to many common security threats
Integrations and integration infrastructure, while essential for facilitating seamless data exchange and system communication, are also susceptible to various security vulnerabilities.
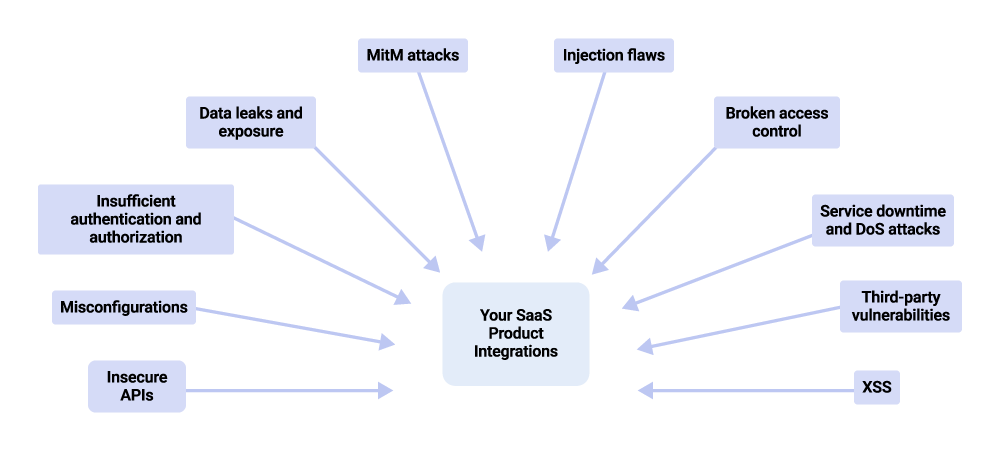
Let's look at these common security threats in more detail:
- Insecure APIs: Since integrations frequently rely on APIs, vulnerabilities in API security can expose sensitive data and system functions to unauthorized access. Common issues include inadequate input validation, insufficient authentication, and insecure data transmission.
- Misconfigurations: Integrations can be complex to configure correctly, and misconfigurations can inadvertently expose endpoints, data, or functionalities that should be restricted, leading to potential security breaches.
- Insufficient authentication and authorization: Weak auth processes can allow unauthorized users to access integrations. Inadequate authorization checks can let users perform actions beyond their permissions.
- Data leaks and exposure: Poorly designed integrations can lead to unintended data exposure. For instance, sensitive information might be logged improperly or transmitted in plaintext, which could be intercepted during transmission.
- Man-in-the-middle (MitM) attacks: If data is not properly encrypted during transmission between integrated systems, it can be vulnerable to interception and alteration by attackers, potentially leading to data theft or manipulation. Improper handling of integration sessions or exposing user browser cookies to attackers can also lead to MitM attacks.
- Injection flaws: SQL injection, command injection, and other types of injection flaws can occur when an attacker sends malicious data as part of a command or query. Integrations that do not properly sanitize input can be vulnerable to these attacks.
- Broken access control: Insufficient restrictions on what authenticated users are allowed to do can lead to unauthorized access to functions and data they should not have access to, potentially allowing them to perform actions detrimental to the integration’s integrity.
- Service downtime and denial of service (DoS) attacks: Overloading integration infrastructure with a high volume of requests, or exploiting specific vulnerabilities to disrupt service, can lead to a denial of service for legitimate users.
- Third-party vulnerabilities: Integrations often connect multiple third-party systems, and vulnerabilities in any one of these systems can potentially compromise the security of every connected system.
- Cross-site scripting (XSS): If the integration involves a web-based management UI, it could be susceptible to XSS attacks, in which malicious scripts are injected into web pages viewed by other users.
Integration security failures can have a huge impact
The impact of security vulnerabilities on companies providing or using SaaS integrations can be significant and multifaceted. Since SaaS integration solutions typically manage data flow between cloud-based and on-premises applications, the implications of these security threats can extend across the entire enterprise.
Here are several key impacts:
- Operational disruption: Security incidents such as service downtime or data breaches can lead to significant operational disruptions. For instance, a successful DoS attack on SaaS integration infrastructure could halt all integration services, impact all dependent business processes, and lead to productivity losses.
- Reputational damage: Data breaches can severely damage a company's reputation. For example, a breach that exposes sensitive customer data due to inadequate API security could lead to negative publicity, customer churn, and a decreased competitive edge.
- Financial loss: Direct costs may include expenses related to incident response, forensic investigations, system repairs, and data recovery. For example, recovery from a denial of service (DoS) attack can require substantial investment in both infrastructure and manpower to mitigate the attack and prevent future occurrences. Indirect costs might include legal fees, fines for non-compliance with regulations, and compensation to affected customers or partners.
- Legal and regulatory consequences: Non-compliance with legal and regulatory standards can result in hefty fines and legal actions. Failure to secure SaaS integrations for businesses operating under regulations like GDPR, HIPAA, or CCPA can lead to legal repercussions and mandatory breach reporting, further tarnishing a company's image.
- Compromise of sensitive data: Vulnerabilities like insecure APIs and injection flaws can lead to unauthorized access and theft of sensitive data, including personal information, intellectual property, and business secrets. The impact extends beyond immediate financial losses to long-term intellectual property theft or strategic disadvantage.
- Loss of intellectual property: Security breaches can lead to the loss of intellectual property, which can be particularly damaging for businesses that rely on proprietary technologies or business processes. This not only impacts competitive advantage but can also affect future revenue streams.
- Strategic setbacks: A security incident can force a business to reconsider or modify its digital transformation strategies, potentially delaying important innovations or enhancements that rely on secure integration functionalities.
- Resource drain: Addressing security vulnerabilities often requires allocation of additional resources for emergency response and long-term security enhancements. This diversion of resources can affect other business areas by delaying projects, increasing operational costs, and placing additional strain on personnel.
Section 3: Implement integration security best practices
Security for integrations starts with design principles
Secure design principles are guidelines that help devs build software that is robust against attacks, protects data integrity, and ensures user privacy. Adhering to these principles during the software development lifecycle for integrations can significantly mitigate security risks.
Here are secure design principles and controls, including aspects of code versioning and control, which integration devs and DevOps should implement:
Principle of least privilege
- Description: Ensure that every integration module, such as a process, a user, or a program, has access only to the information and resources necessary for its legitimate purpose.
- Implementation: Apply this principle to system processes and integration functionalities, ensuring services have only the minimum permissions they need to perform their intended functions.
Fail-safe defaults
- Description: Base access decisions on permission rather than exclusion, meaning if the condition isn't explicitly allowed, it should be denied by default.
- Implementation: Design integration components so that if a security decision point fails, the default result is a denial of access. Configure systems to automatically default to secure settings.
Economy of mechanism
- Description: Keep the design as simple and small as possible. Complex designs increase the chance of errors, failures, and security breaches.
- Implementation: Break down large, complex integrations into smaller, manageable functions to simplify security implementation and make it easier to find and fix security bugs.
Complete mediation
- Description: Every access to every object must be checked for authority, ensuring all accesses are authorized, monitored, and controlled.
- Implementation: Implement checks at every integration access point, including validating user input at both client-side and server-side to prevent SQL injection and other injection flaws.
Open design
- Description: The design should not be secret; security should not rely on obscurity but on the possession of specific, more easily protected keys or passwords.
- Implementation: Where possible, use well-known and tested security algorithms and open standards for integrations, ensuring that the security mechanisms are public and robust.
Defense in depth
- Description: Employ multiple layers of security controls (defense) throughout the software to create a layered defense.
- Implementation: Combine various security measures like firewalls, anti-virus software, and intrusion detection systems with application-specific measures like input validation and encryption.
Least common mechanism
- Description: Minimize the amount of mechanisms common to more than one user and depended on by all users.
- Implementation: Reduce shared integration resources among users to limit the chances of a security breach affecting multiple parties.
Psychological acceptability
- Description: Security mechanisms should not make the resource more difficult to access than if the security mechanisms were not present.
- Implementation: Make integration security user-friendly, such as implementing easy-to-use yet secure user authentication procedures.
Secure defaults
- Description: Systems should be secure by default, requiring users to actively disable security features if they choose to operate with less security.
- Implementation: Deploy integrations with the most secure configuration as the default option, disabling all non-essential services and settings.
Code versioning and control
Description
Code versioning and control involve managing changes to code with version control systems to track modifications, prevent conflicts, and maintain the integrity and history of integration code.
Implementation
- Use version control systems (VCS): Implement tools like Git to manage integration code repositories. This allows developers to track revisions, branch out, and merge code changes efficiently.
- Branch management: Define a clear branch strategy (e.g., GitFlow) to manage features, hotfixes, and releases, ensuring that changes are isolated in development and then merged systematically into main branches.
- Code review process: Enforce an integration code review process where peers review each other's code for security flaws and bugs before merging changes, enhancing code quality and security.
- Automated build and integration: Integrate continuous integration/ continuous deployment (CI/CD) pipelines to automate building and testing of integration changes, ensuring that new commits do not introduce security issues or bugs.
- Access control: Restrict access to integration code repositories and ensure that only authorized personnel can change critical parts of the codebase, aligning with the principle of least privilege.
Protecting integration data integrity is foundational
Protecting the integrity of data passed via integrations involves ensuring that the data is not altered or tampered with during transmission or storage.
Some key strategies and techniques commonly used to protect data integrity within integrations and related infrastructure are:
- Encryption: Encrypting data both in transit and at rest is fundamental to protecting its integrity. Encryption ensures that even if data is intercepted, it cannot be read or altered without the decryption key. Common protocols for encrypting data in transit include TLS (Transport Layer Security) and SSL (Secure Sockets Layer). You'll want to ensure your integration infrastructure provides you with at least TLS 1.2 or greater for data in transit. Some of the cyphers in TLS 1.2 are considered weak, so making sure your browsers and access clients use TLS 1.3 is best. Employing encryption algorithms such as AES (Advanced Encryption Standard) for data at rest is common practice.
- Data validation and sanitization: Implement robust input validation to ensure only properly formatted data is processed and stored. This helps prevent malicious data from being injected into the system, which could compromise data integrity. Sanitizing data inputs to remove or encode potentially hazardous data can also prevent injection attacks such as SQL injection, XSS, or command injection.
- Hashing and digital signatures: Use cryptographic hash functions to verify data integrity. A hash function converts data into a fixed-size string of bytes (the hash) that acts as a data fingerprint. Any change in data changes the hash. Digital signatures go a step further by allowing the verification of the data's integrity and sender's identity, providing non-repudiation.
- Access controls: Implementing strict access controls ensures only authorized users and systems can read or modify integration data. This includes using role-based access control (RBAC) systems to enforce the principle of least privilege, minimizing each user's access to the minimal level of data and actions needed for their role.
- Audit trails: Maintain comprehensive logs of data access and changes to integrations. Audit trails help identify and rectify unauthorized or accidental data changes, providing a mechanism for accountability and recovery.
- Regular updates and patch management: Keeping integration infrastructure up to date with the latest security patches is crucial. Many data breaches and integrity issues stem from exploiting vulnerabilities in outdated software. Further, making sure your integration code doesn't have vulnerabilities is also crucial. Vulnerable code and systems lead to an exploited integration and ultimately data compromise.
- Data redundancy and backup: Implementing data redundancy and regular backups can ensure integration data integrity and availability. Backups are a reliable recovery solution in case data is corrupted or lost. It's important to secure and regularly test backups to ensure they are up to date and effective.
- Network and system security: Secure the network infrastructure using firewalls, security groups, access control lists, intrusion detection systems (IDS), intrusion prevention systems (IPS) to prevent unauthorized access and mitigate potential data integrity threats. Continuously monitoring for anomalies and knowing what is normal vs abnormal, creating security alerts around abnormal situations, and getting those alerts to the correct security personal so they can triage them and perform incident response if necessary. Using a post incident analysis procedure to discover root cause with digital forensics and leveling up the whole security detection and response process is critical in today's threat atmosphere.
- End-to-end integrity checks: Conduct regular end-to-end integrity checks within the integration process. This can involve periodically verifying that data in your databases matches securely generated hashes or checksums.
Integration authentication and authorization are crucial
Robust authentication and authorization mechanisms are crucial to ensure secure access and operations. Here are some key components and strategies to consider when implementing authentication and authorization for SaaS integrations:
- Multi-factor authentication (MFA): This security system requires more than one method of authentication from independent categories of credentials to verify the user's identity for a login or other transaction. MFA could include something the user knows (password), something the user has (security token), and something the user is (biometrics).
- OAuth 2.0: OAuth is an open standard for access delegation. It is commonly used by internet users to grant websites or applications access to their information on other websites without giving them the passwords. This is particularly useful with integrations for authorizing interactions between applications without exposing user credentials.
- Role-based access control (RBAC): RBAC restricts system access to authorized users. For SaaS integrations, roles can be defined for different types of users (e.g., admin, developer, end-user) to control access to functions within the integration or integration infrastructure based on those roles.
- JWT (JSON web tokens): JWTs are an open standard (RFC 7519) that defines a compact and self-contained way for securely transmitting information between systems as a JSON object. This information can be verified and trusted because it is digitally signed. JWTs can be signed using a secret (with the HMAC algorithm) or a public/private key pair using RSA or ECDSA.
- Secure token service (STS): An STS issues security tokens that authenticate a user's identity and authorize their access level. This service can also renew and validate tokens, ensuring authentication is secure and current.
- API gateways with authentication: An API gateway can act as a control point for authentication and authorization, ensuring that only valid and authorized requests access integration services. It can handle OAuth tokens, API keys, JWTs, and other authentication and authorization checks.
- Attribute-based access control (ABAC): This approach defines access rights based on attributes associated with user accounts, allowing for a more granular and context-specific access control than RBAC. This can help integrations manage dynamic and complex permissions for different integration flows and services.
- API keys: Although less secure than methods like OAuth, API keys are a simple way to control access to APIs for integrations. For enhanced security, API keys should always be used with other security measures, such as HTTPS, to ensure that the keys are transmitted securely. Keys should also be rotated every 90 days, at a minimum, in case they are compromised or discovered.
- Session management: Proper management of integration session lifetimes, ensuring that sessions are securely established and terminated, can prevent unauthorized access. This includes setting timeouts for sessions and regularly re-authenticating users. Poor session expiration can lead to man-in-the-middle attacks that gain access to a session and masquerade as the proper session owner.
- Audit trails and monitoring: Keeping detailed logs of authentication and authorization events can help detect and respond to integration security incidents more effectively. Monitoring these logs for abnormal access patterns or unauthorized access attempts is critical for maintaining security.
Legal and regulatory compliance must be included
Ensuring compliance with legal and regulatory requirements is crucial for any organization, particularly those handling sensitive and personal data. Adhering to established security and privacy frameworks not only helps in meeting these requirements but also in building trust with customers and partners.
Below, we'll explore key security and privacy frameworks and discuss their relevance.
Security frameworks

There are nearly as many security frameworks as programming languages. We'll highlight a few of the big ones pertaining to integrations.
SOC 2 (Service Organization Control 2)
- Purpose: Designed for service providers storing customer data in the cloud, SOC 2 focuses on five trust service principles: security, availability, processing integrity, confidentiality, and privacy.
- Relevance: Provides a benchmark for managing data based on structured criteria that ensure security, availability, and confidentiality. Compliance helps reassure clients that a service provider manages data flowing through its systems with high integrity and security.
NIST (National Institute of Standards and Technology) Cybersecurity Framework
- Purpose: Provides a policy framework of computer security guidance for how private sector organizations in the U.S. can assess and improve their ability to prevent, detect, and respond to cyber attacks.
- Relevance: It offers comprehensive guidance for digital security, including tools, standards, and best practices for managing cybersecurity-related risk. Its flexible nature allows it to be implemented according to the organization's specific needs and risk profile.
ISO (International Standards Organization) 27001
- Purpose: ISO 27001 is an international standard for managing information security. It specifies requirements for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). The standard is designed to help organizations secure their information assets.
- Relevance: ISO 27001 provides a systematic approach to managing sensitive company information so that it remains secure. It includes people, processes, and IT systems by applying a risk management process. Compliance with this standard helps organizations protect their information systematically and cost-effectively, based on confidentiality, integrity, and availability principles. It is particularly relevant in sectors where the protection of information is critical, such as finance, health, public, and IT sectors.
CCM (Cloud Controls Matrix)
- Purpose: Developed by the Cloud Security Alliance (CSA), the CCM is a cybersecurity control framework for cloud providers and consumers. It serves as a comprehensive tool for assessing a cloud provider's overall security risk. The CCM provides a detailed understanding of security concepts and principles aligned to the Cloud Security Alliance guidance in 13 domains.
- Relevance: The CCM is designed to provide fundamental security principles to guide cloud vendors and to assist prospective cloud customers in assessing the overall security risk of a cloud provider. The matrix spans important domains such as compliance, data governance, facility security, human resources, information security, legal issues, operations management, risk management, release management, resilience, security architecture, and identity and access management. These domains are addressed by specific controls that align with industry-accepted security standards, regulations, and controls frameworks, such as ISO 27001/27002, ISACA COBIT, PCI, NIST, and HIPAA. This makes the CCM a versatile and widely applicable framework that can be used across various cloud models, including IaaS, PaaS, and SaaS, providing a thorough mechanism for ensuring that cloud services are secure and compliant with global standards.
Privacy frameworks

Privacy frameworks are becoming more common as jurisdictions sign them into law. Here are a couple of the main ones for integrations:
GDPR (General Data Protection Regulation)
- URL: https://gdpr.eu/
- Purpose: Regulates data protection and privacy in the European Union and the European Economic Area, but it also addresses the transfer of personal data outside the EU and EEA.
- Relevance: Sets guidelines for the collection and processing of personal information of individuals. It emphasizes transparency, security, and accountability by data processors and controllers, giving individuals control over their personal data.
HIPAA (Health Insurance Portability and Accountability Act)
- Purpose: U.S. legislation that provides data privacy and security provisions for safeguarding medical information.
- Relevance: Protects sensitive patient health information from being disclosed without the patient's consent or knowledge, thus securing personal health information both in paper and electronic forms.
General data security and privacy considerations
When dealing with data security and privacy, the following considerations must be top of mind:
- Data minimization: Collect only the data necessary for the specified purpose. This limits the risk of exposure.
- Data encryption: Use strong encryption standards in transit and at rest to protect sensitive data from unauthorized access.
- Access controls: Implement stringent access controls and authentication mechanisms to ensure only authorized personnel can access sensitive data.
- Regular audits: Conduct regular audits and assessments to ensure compliance with security policies and regulatory requirements.
- Incident response plans: Develop and maintain an effective incident response plan to quickly address any data breach or security incident.
- Training and awareness: Regularly train employees on data protection practices, emphasizing the importance of securing personal and sensitive information.
- Data integrity and availability: Implement data integrity checks and ensure data availability through proper backup and disaster recovery processes.
Error handling and logging enable efficient issue resolution
Error handling and logging are crucial for robust integration security, particularly for a SaaS integration environment where multiple systems interact. Properly managing error handling and logging ensures the prevention of sensitive information leakage and the ability to trace and rectify issues efficiently.
Errors to monitor and log for SaaS integrations
- Authentication and authorization failures: Log all failed authentication attempts, including timestamp, source IP, and the user ID attempted. This can help identify potential brute-force attacks or unauthorized access attempts. Authorization failures should also be logged to detect any attempts to access resources beyond a user's permissions, which could indicate a misconfiguration or a malicious insider.
- Data validation errors: Any data that fails to meet predefined schemas or validation rules should be logged. This includes type mismatches, format errors, and size limitations which could indicate incorrect or potentially malicious input.
- Service downtime and availability issues: Any service disruptions or performance degradations. This includes timeouts, service unreachable errors, and unexpectedly long response times, which can indicate a system overload or a denial-of-service attack.
- Integration flow errors: Processing logic errors, such as failed transformations or routing errors, should be logged with detailed information about the workflow step and data involved (without logging sensitive data).
- Configuration changes: Any configuration changes, especially those related to security settings or integration flows, should be logged to track who made the change and what was changed. This is crucial for auditing and understanding the impact of the changes.
- API rate limiting violations: Log any exceedance events if your integration enforces API rate limits. These could signal attempts to flood services with too many requests or misconfigurations in connected applications.
Strategies for effective error handling and logging
- Use structured logging: Implement structured logs that make searching and analyzing data easier. Use a consistent format with key-value pairs that include necessary metadata for each event.
- Sensitive data masking: Ensure that logs do not contain sensitive information. Mask or tokenize personal data and credentials before they are written to logs to prevent data leakage.
- Centralized logging: Use a centralized logging system that aggregates logs from all services and components of your integrations. This simplifies monitoring and analysis, making it easier to correlate events across different parts of the system.
- Real-time alerting: Set up real-time alerts based on specific log events, such as repeated authentication failures or configuration changes. Use monitoring tools to analyze log streams and trigger alerts when certain thresholds or patterns are detected.
- Regular audits of logs and alerts: Periodically review logs and the alerting system to ensure they capture the necessary information and that the alert logic aligns with current threat patterns and business needs.
- Access controls for logs: Restrict log access to only those roles that need it. Logs can contain sensitive information, and access to them should be guarded as carefully as access to the live data.
- Retention policies: Define and enforce data retention policies for logs to comply with legal and regulatory requirements while ensuring that old logs do not accumulate unnecessarily, creating security and operational risks.
Conclusion
In this guide, we've laid out what it takes to safeguard SaaS integrations and the data flowing through them.
We've emphasized the importance of robust authentication methods like OAuth and API keys, comprehensive input validation, and diligent management of credentials and connections to prevent unauthorized access and data breaches.
We've also underscored the necessity of adhering to regulatory standards such as GDPR and HIPAA, which are crucial for ensuring data privacy and security.
Additionally, we have highlighted the critical role of comprehensive logging and monitoring systems that enable the swift detection and remediation of security incidents.
Even though this guide is an overview, it's still a lot to take in. It may even seem overwhelming if you are new to security (or integrations). Addressing all the security concerns as you define the infrastructure for your integrations and then keeping them in mind as you build, deploy, and manage those integrations could be a full-time job for several people.
The good news is that using an embedded iPaaS designed in accordance with security best practices can remove much of the integration security burden from your team, allowing them to focus on everything else your customers need in their integrations.
To learn about Prismatic's industry-leading embedded iPaaS, visit prismatic.io.
We'd love to hear from you if you have questions on integration security as you prepare to build your product's first integrations, reexamine your existing integration strategy through a security lens, or consider implementing an embedded iPaaS to get things moving more quickly.
Additional resources
To learn more about integration security and related topics, here are some resources we recommend.
White papers and technical reports
- Cloud Security Alliance (CSA) (https://cloudsecurityalliance.org/): CSA offers multiple research artifacts that discuss security best practices for cloud environments, including the Cloud Controls Matrix (CCM) and security guidance for critical areas of focus in cloud computing.
- SANS Institute InfoSec Reading Room (https://www.sans.org/security-resources/): Contains white papers on various cybersecurity topics that are practical and detailed for technical implementation.
Technology blogs and industry articles
- AWS Security Blog (https://aws.amazon.com/blogs/security/) and Microsoft Security Blog (https://www.microsoft.com/en-us/security/blog/): Provide insights into security practices, case studies, and innovations in cloud security pertinent to integrations.
- Google Cloud Blog (https://cloud.google.com/blog/): Offers articles on security trends and best practices in the cloud, which can be directly applicable to managing security in SaaS integration environments.
- BuzzSec Security and Threat Intelligence Blog Collection (https:// buzzsec.blogspot.com/) One-stop-shop for information security and threat intelligence news.
Professional and technical forums
- Stack Overflow (https://stackoverflow.com/) and GitHub Discussions (https://github.com/orgs/community/discussions/): For practical, community-driven advice and troubleshooting on security issues.
- Security Pillar - AWS Well-Architected Framework (https://docs.aws. amazon.com/wellarchitected/latest/security-pillar/welcome.html): For detailed guidance on designing and operating reliable, secure systems on AWS.
About the author
Buzz Hillestad is a seasoned IT and cybersecurity professional with a career spanning nearly three decades. Since pivoting to a specialized focus on security in 2004, Hillestad has become a leading authority in the field.
He currently serves as the Information Security Officer (ISO) at Prismatic, where he concentrates on orchestrating and overseeing the organization's robust cybersecurity strategies for the company’s market-leading embedded integration platform. In addition to his undergrad degree in Computer Information Systems in Business, he is also certified as a GIAC Certified Forensics Examiner (GCFE).