OAuth 2.0 Client Credentials Grant Type
The client credentials grant type, also known as machine-to-machine (M2M) authentication, enables server-to-server communication without user interaction. This flow is commonly used when your integration needs to access a third-party API on behalf of your application rather than an individual user.
Client credentials grant type overview
The OAuth 2.0 Client Credentials grant type is sometimes called the Machine-to-Machine (M2M) grant type and allows your application to communicate with a third-party directly.
The Client Credentials flow is different from the Authorization Code flow in a couple of key ways:
- Customers do not work through a consent screen. Rather, customers generate their own client ID / secret key pair and explicitly grant permissions to the key pair they generate.
- Key pairs are generally not associated with a specific user. Instead, the key pairs have permissions to access certain resources in their account.
- This flow generally does not require an approval process from the third-party app, since you don't create an OAuth 2.0 app. Instead, your customer logs in to their account to create the key pair that you will use.
Additional resources: https://oauth.net/2/grant-types/client-credentials/
How does the client credentials grant type work?
At a high level, the OAuth 2.0 client credentials flow works like this:
- You ask your customer to log in to their third-party app account and generate a Client ID / Client Secret key pair. You ask them to grant that key pair a certain set of permissions.
- Your customers enter their key pair in your integration's config wizard.
- Your app exchanges the key pair using the third-party app's token URL for an access token that you can use to interact with your customer's third-party account.
The Prismatic OAuth service takes care of the token exchange for you.
Adding an OAuth 2.0 client credentials connection to an integration
When your customer configures an instance of your integration, they'll need to create their client ID and secret key pair and enter those values into your configuration wizard. If your token URL is the same for all users, we recommend that you mark that input as only organization-visible (so your customers don't risk editing it). You can do the same with the scopes input.
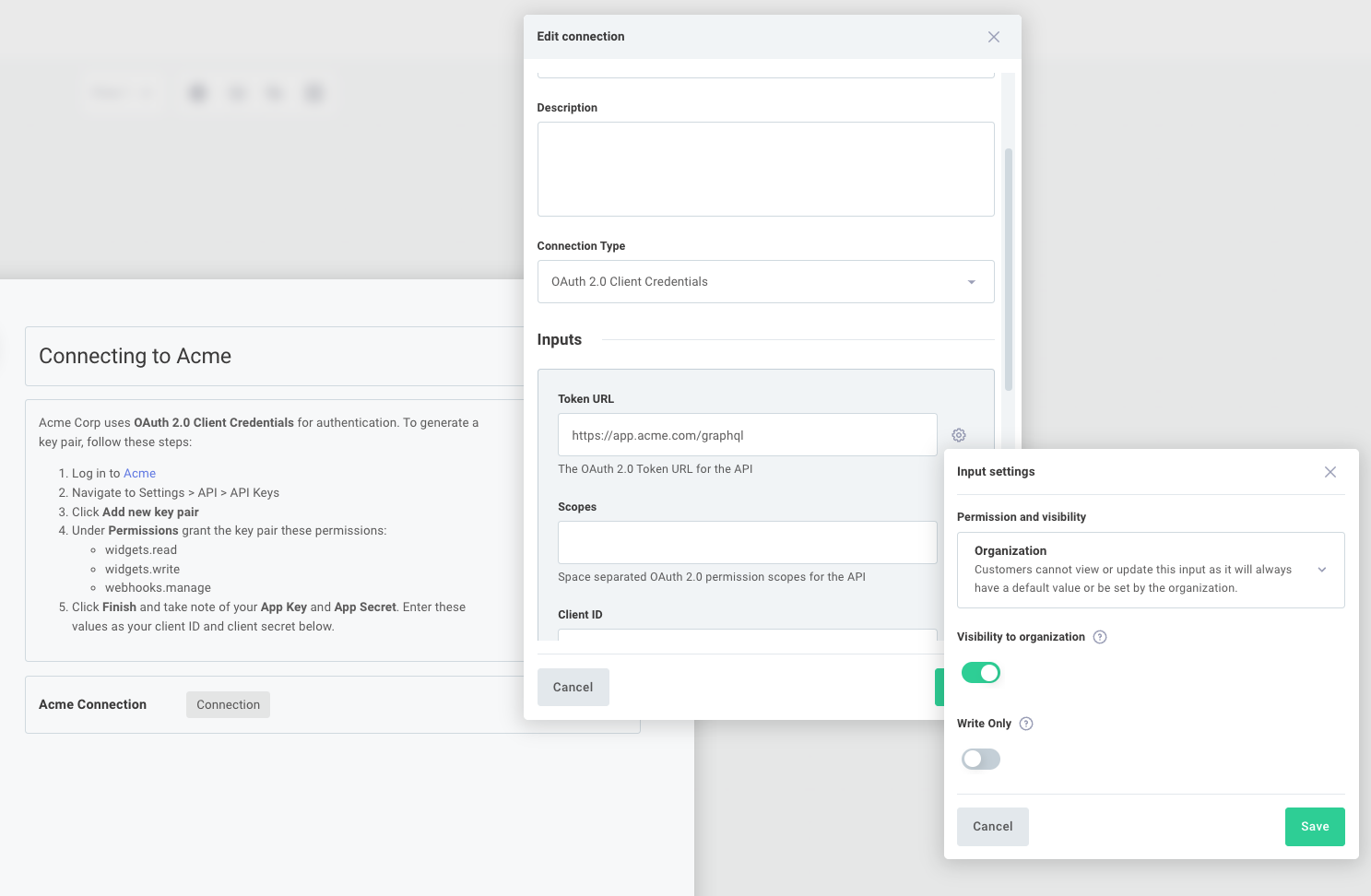
Creating a client ID and secret and assigning the key pair a set of permissions can be a daunting task for a customer user. You can add helpful instructions including links to documentation and screenshots to guide the user through the key pair creation process.
Configuring a client credentials connection
When your customer walks through your configuration wizard, they will be prompted to enter their Client ID and Client Secret. Clicking Connect will cause Prismatic's OAuth 2.0 service to exchange their key pair with the third-party API for an access token that your integration will then begin to use.
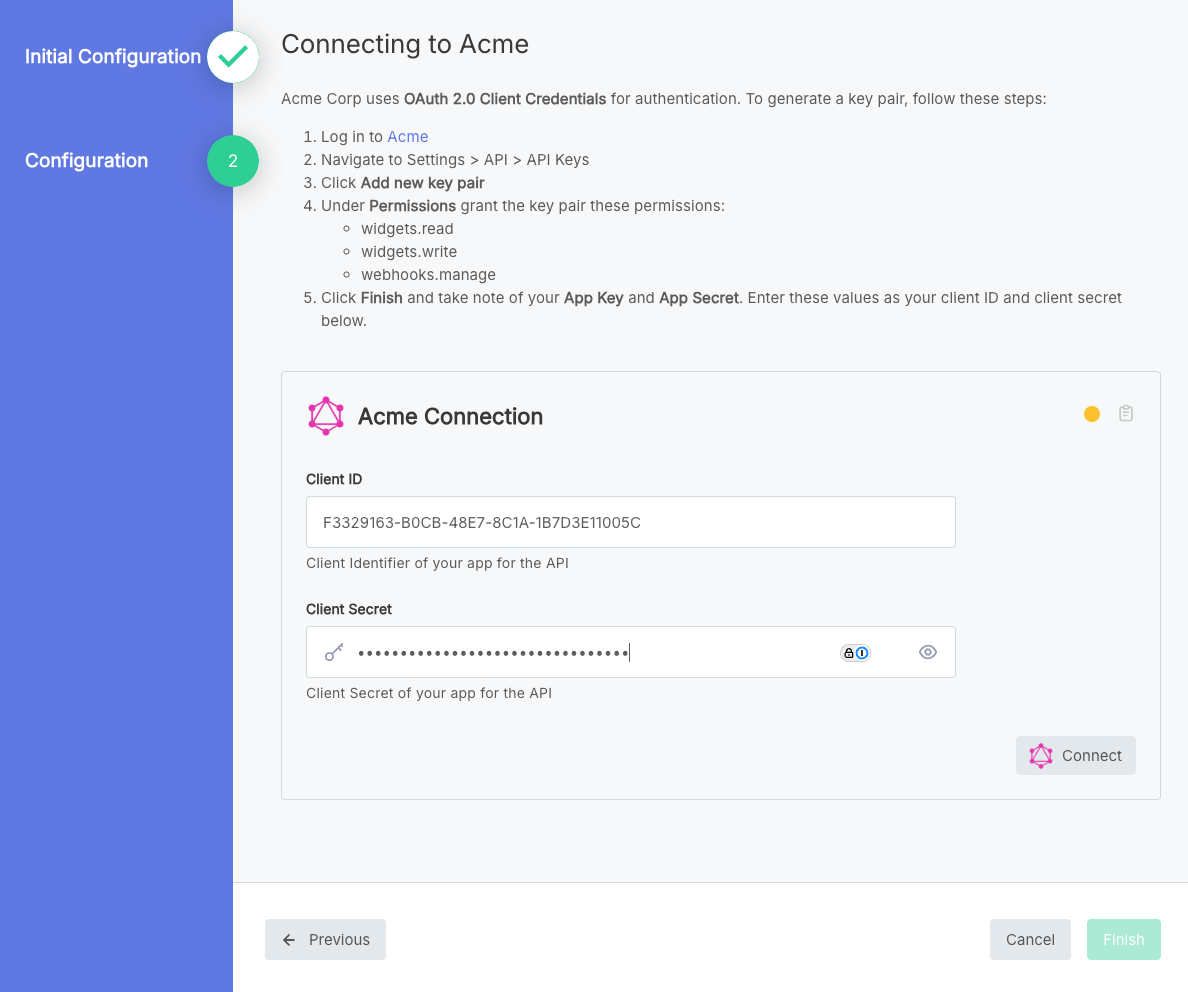
After clicking Connect, the user will either see an "Authorization Complete" or an "Authorization Failed" screen, depending on whether their connection was successful or not. If you'd like this screen to close immediately, see these documentation files.