Connections Overview
Connections contain the information necessary for the steps in your integration to connect to third-party apps and services. A connection is made up of fields for things like usernames, passwords, API keys, OAuth 2.0 secrets, host endpoints, API versions, and more - whatever a component needs to know to connect to an outside service.
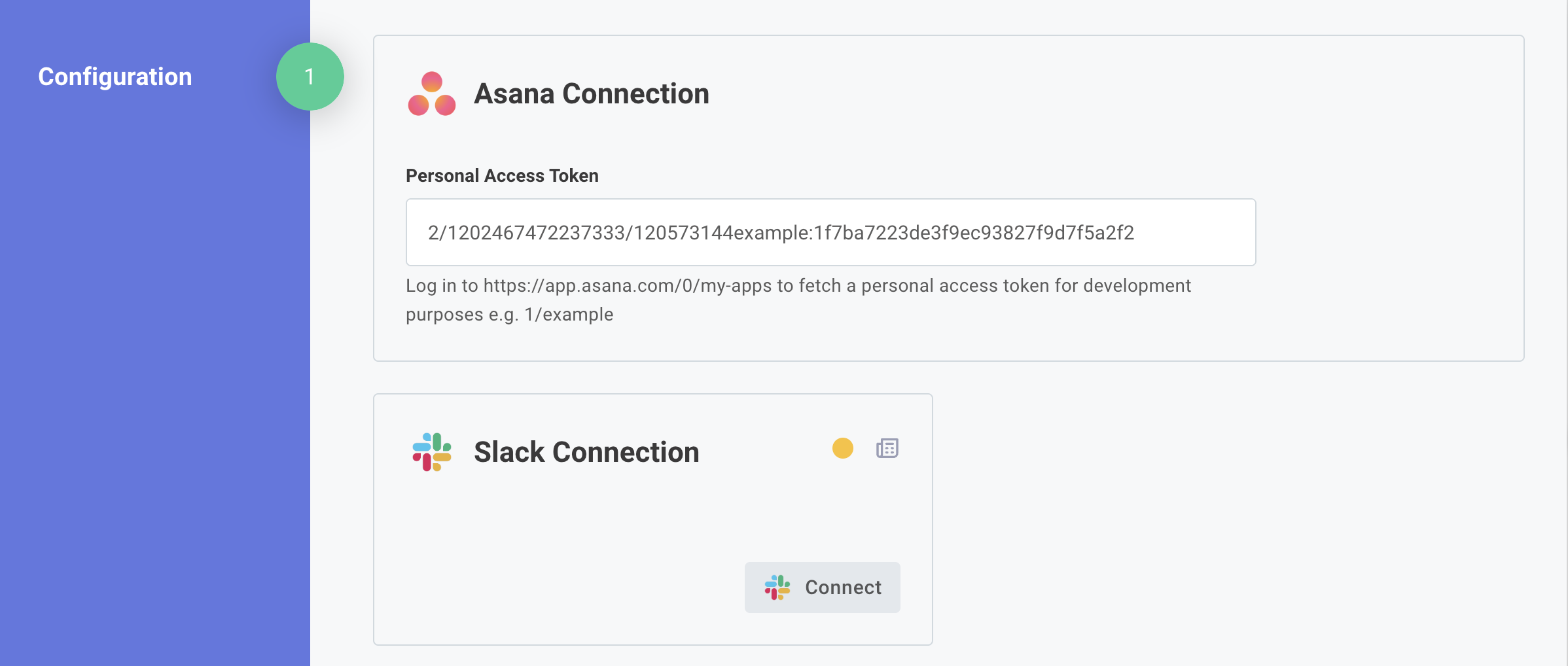
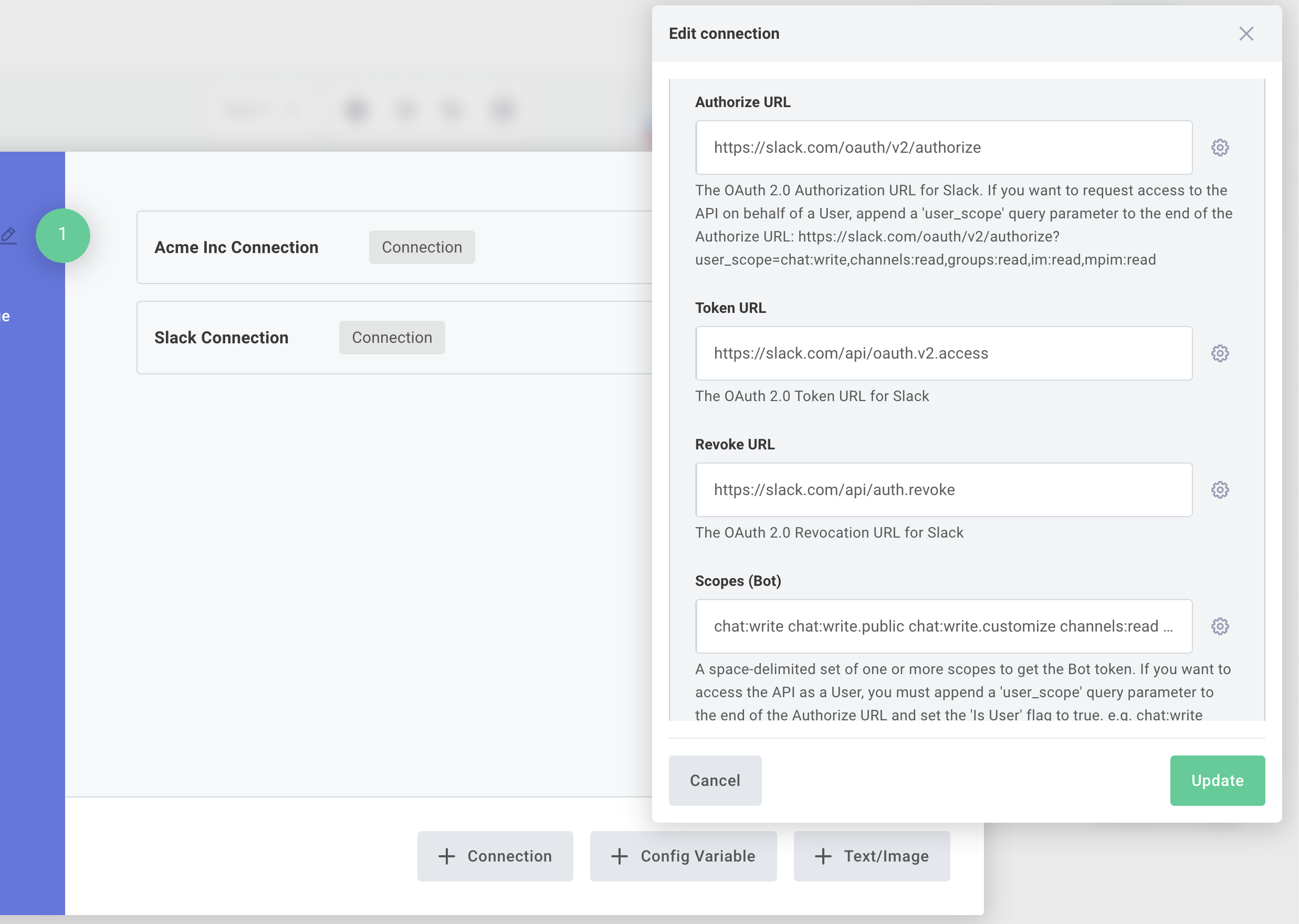
For example, an Asana personal access token requires a single API key, and the Slack connection requires an OAuth 2.0 authorize URL, token URL, client ID, and client secret (though end users will only see a single "Connect" button when they deploy an integration).
Connections are generally presented to customer users on the first page of your integration's configuration wizard, but you can also set up the connection on your customers' behalf if you know the values the connection requires.
Choosing a connection type
Prismatic offers two approaches to managing connections in your integrations:
Integration-specific connections
Integration-specific connections are configured directly within a single integration. They're the fastest way to add a connection when you need it for only one integration and your customers will enter their credentials during configuration.
Best for: One-off integrations where connection reuse isn't needed.
Reusable connections
Reusable connections (also called integration-agnostic connections) are centrally managed and can be used across multiple integrations. They're the better choice when you need to reuse credentials, manage connections on behalf of customers, or enable connections in the embedded workflow builder.
Best for: Connections shared across multiple integrations or managed centrally by your organization.
Learn more about what reusable connections are and when to use them.
Comparison
| Feature | Integration-Specific | Reusable (Integration-Agnostic) |
|---|---|---|
| Scope | Single integration | Multiple integrations |
| Management | Per integration | Centralized |
| Test credentials | Configured per integration | Centralized test connection |
| Best for | One-off integrations | Repeated use across integrations |
For detailed information:
- Learn about integration-specific connections
- Learn about reusable connections and the three types available