Organization Team Members
Organization users are team members employed by your company. They are responsible for building, deploying, and supporting integrations for your customers, and can be granted permissions based on their assigned role.
Organization team member roles
Organization users can be assigned a variety of roles:
- An organization owner is a super-user who can manage all aspects of an organization (users, customers, integrations, etc.).
- An organization admin has all the permissions of an owner, except the ability to make changes to the organization itself. This role is typically granted to user management teams (like your IT team).
- An organization integrator can manage customers, integrations, and instances. Most developers, DevOps, and implementation technicians will have this role.
- An organization restricted integrator can manage customers, integrations, and instances, but cannot view instance logs, step results, or customer-scoped connections. This role is suitable for team members who need to manage integrations but should not have access to sensitive runtime data or customer credentials.
- An organization guest is a read-only user who can view information about customer instances but cannot modify anything. This is suitable for support technicians who need to view logs but should not modify instance configurations.
- An organization customer manager has limited permissions and can manage customers but cannot view or manage their instances. This is appropriate for support users who should not have access to customer instance configurations.
- An organization third-party user is used when you are integrating with a third-party app or service and would like to grant limited access to a user from that third-party to specific integrations, components, or customers. The third-party role is described in more detail below.
| Owner | Admin | Integrator | Restricted Integrator | Guest | Customer Manager | Third-Party | |
|---|---|---|---|---|---|---|---|
| View Customers | x | x | x | x | x | x | ? |
| View Customer Users | x | x | x | x | x | x | |
| View Customer Instances | x | x | x | x | x | ||
| View Alert Monitors | x | x | x | x | x | ||
| Manage Customers | x | x | x | x | x | ||
| Manage Customer Users | x | x | x | x | x | ||
| Manage Components | x | x | x | x | ? | ||
| Manage Instances | x | x | x | x | ? | ||
| Manage Integrations | x | x | x | x | ? | ||
| View instance logs ** | x | x | x | ||||
| View instance step results ** | x | x | x | ||||
| View scoped connections ** | x | x | x | ||||
| Manage Organization Users | x | x | |||||
| Configure Embedded Themes | x | x | |||||
| Manage Embedded Settings | x | x | |||||
| Configure Log Streaming | x | x | |||||
| Manage Organization | x |
** If you would like to prevent access to logs, step results, and customer-scoped connections for all users, reach out to Prismatic Support to enable the "Restrict Sensitive Data Access" organization setting.
Managing organization users
Only organization users with admin or owner roles can manage organization users.
To manage organization users in the web app, click Settings on the left-hand sidebar, and select the Team Members tab.
Listing organization users
- Web App
- CLI
- API
Organization users are listed under the Team Members tab. You can filter users by typing a name into the search bar at the top of the page. You can also filter by email address by clicking the Filter link to the right of the search bar.
You can list users via CLI using the organization:users:list subcommand.
prism organization:users:list
Name Email
──────────────── ──────────────────────────
James Patton james.patton@progix.io
Samantha Johnson samantha.johnson@progix.io
Ed Davis edward.davis@progix.io
Kristin Henry kristin.henry@progix.io
Alex Cooper alexander.cooper@progix.io
List users by querying the users field on organization):
query {
organization {
users {
nodes {
id
name
email
}
}
}
}
Adding organization users
- Web App
- CLI
- API
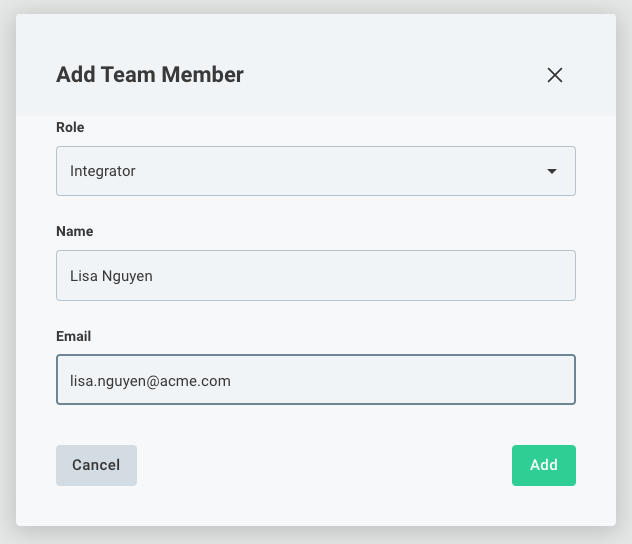
From the Team Members tab, click the + Add team member button in the upper-right. Select an appropriate role for the new user (see above for permissions), and provide a name and email address for the user.
Management of organization users is performed through the prism organization:users subcommands.
You can find the role IDs you are allowed to grant using organization:users:roles.
ROLE_ID=$(prism organization:users:roles \
--columns id \
--no-header \
--filter 'name=Integrator')
prism organization:users:create \
--email 'susan.smith@progix.io' \
--name 'Susan Smith' \
--role ${ROLE_ID}
To create an organization user, you will need the ID of the role you want to assign:
query listOrganizationRoles {
authenticatedUser {
grantableRoles(roleType: ORGANIZATION) {
id
name
description
}
}
}
Once you have the role ID, use the createOrganizationUser) mutation to create a new organization user:
mutation {
createOrganizationUser(
input: {
name: "Susan Smith"
email: "susan.smith@progix.io"
role: "Um9sZTpmYzE0ODIwNC1mZmQxLTQxMWUtYmRlYS1iNmFmYzM4YmViOGE="
}
) {
user {
id
}
}
}
After creating the new user, they will receive a confirmation email with a link to set up their profile and password.
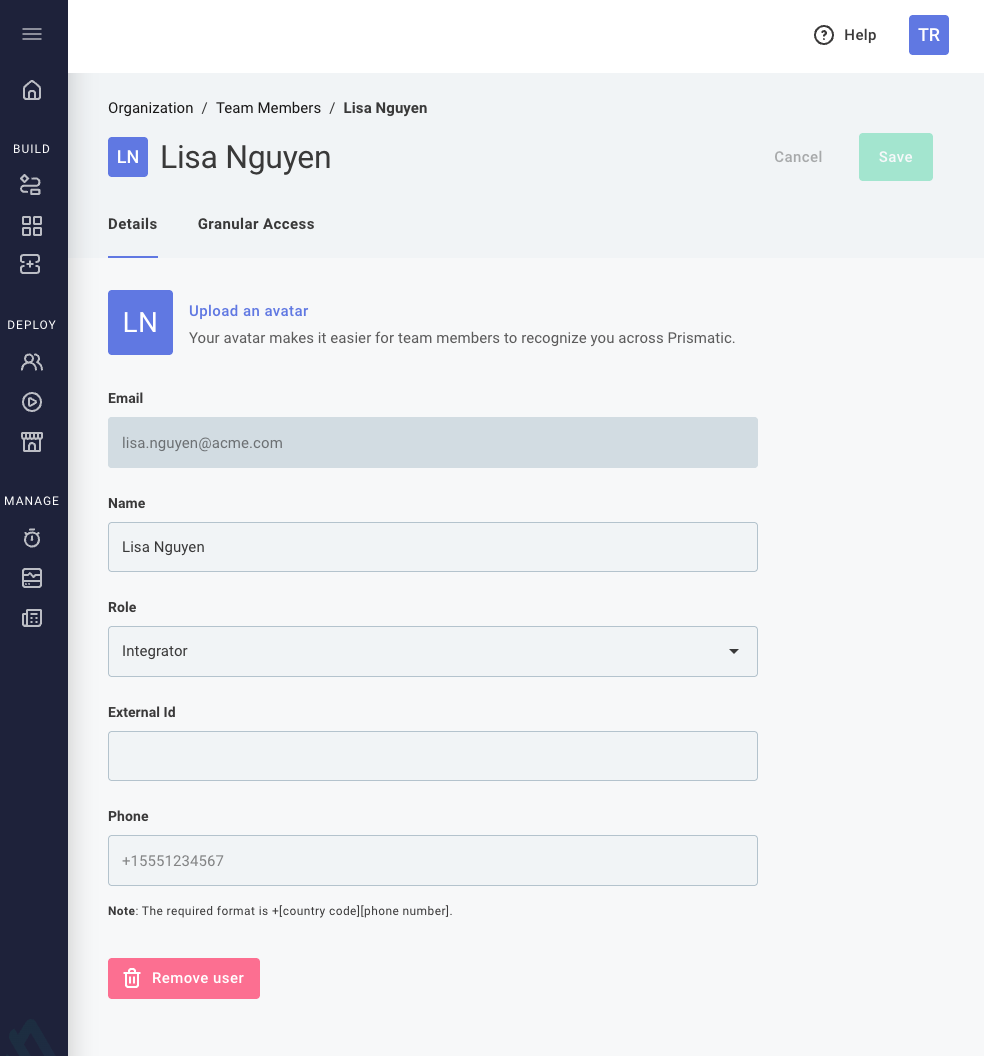
Changing an organization user's role, name, avatar, or phone number
From the Team Members tab, click the name of a user. You can change the user's role, name, phone number, or avatar under the Details tab. After making changes, click Save to apply your updates.
Deleting organization users
- Web App
- CLI
- API
From the Team Members tab, click the name of a user. Select the Details tab within that user's page and click the Delete user button at the bottom of the page. Enter the Confirmation text and click Remove user to confirm removal.
USER_ID=$(prism organization:users:list \
--columns id \
--no-header \
--filter 'email=susan.smith@progix.io')
prism organization:users:delete ${USER_ID}
To delete an organization team member, use the deleteUser) mutation:
mutation {
deleteUser(
input: { id: "VXNlcjpiMmNmNmY5MS1iMjljLTRlODUtOTc1My04NWE0NGM2ZDE2YzE=" }
) {
user {
id
}
}
}
Third-party users
It is often necessary to involve people from third-party vendors as you build, test, and debug your integrations. Granting third-party vendors the ability to view and test specific integrations and components accelerates development and ensures all stakeholders remain aligned regarding development progress and data flow between systems.
Creating third-party users
Organization users with admin or owner permissions can create new organization-level users with the third-party role. This role is highly restricted - by default, third-party users can only edit their own profile information and view built-in components. They cannot view information about your custom components, integrations, or customers. Once created, you can grant additional permissions to allow interaction with specific resources.
You can create a third-party user as you would any other organization-level user: click Settings on the left-hand sidebar, then click + Add team member. Assign the new user the Third-Party role.

Granular access for third-party users
To grant access to specific resources, like integrations, custom components or customers, click Settings on the left-hand sidebar and then Team Members. Select the third-party user you would like to grant access to, and click into the Granular Access tab.
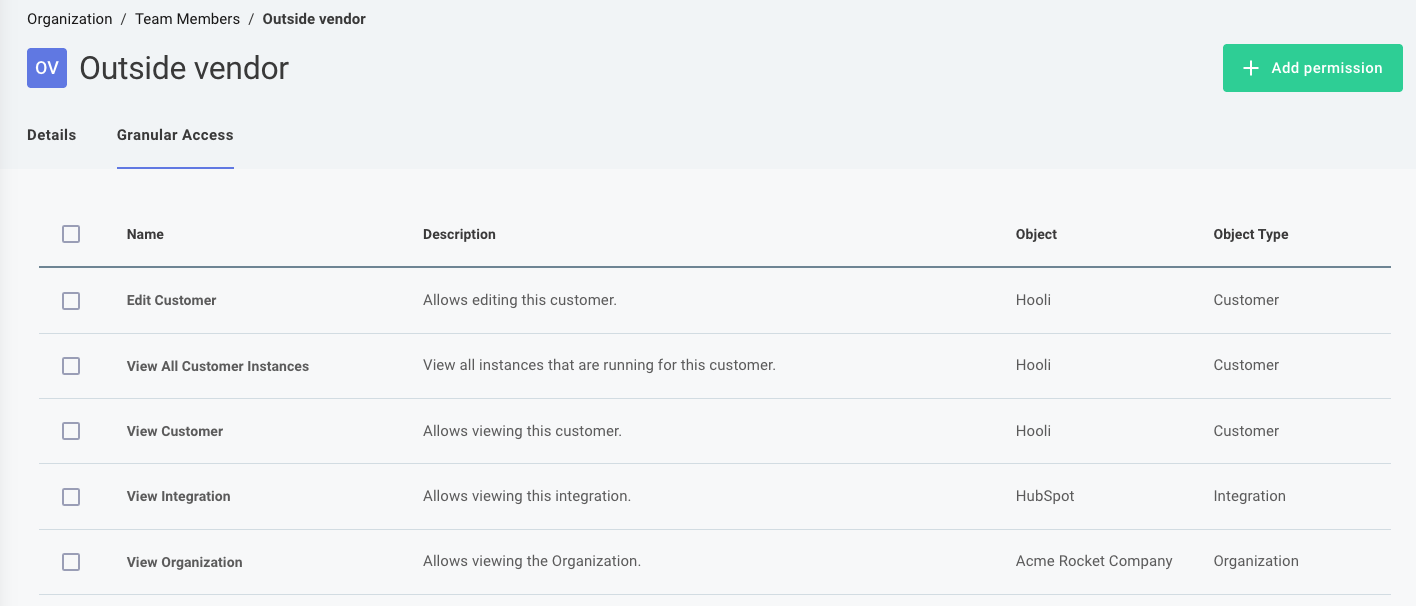
From here, you can grant the user access to specific integrations, components, or customers by clicking the + Add permission button on the top-right.

Integration access
The most common use case for third-party users is to allow a third-party vendor to view, and possibly edit and test an integration. That way, they can test invoking an integration in Prismatic from their third-party service and can verify that the data the integration receives is in the format you agreed upon.
Giving integration access to a third-party vendor also allows you to see what sort of attempts are being made on their end to make sure the integration works. You can view logs of each test a third-party vendor performs to give you a sense of how their side of the integration development is progressing, and if and when you jump on calls with your mutual customer and the third party, you can test and debug issues quickly (rather than relying on email chains that drag on for weeks).
To grant a third-party vendor access to a specific integration, select Integration from the + Add permission dialog, then search for and select the integration you want to give permissions for.
On the next screen select the types of permissions you would like to grant for that integration. If you would like the third-party user to be able to see the integration in their Integrations list view, select View Integration. If you would like the third-party user to be able to edit the integration, select Edit Integration.
The third party user will then be able to see the integration that they've been granted permission to see, but all other integrations will remain hidden from them. This is handy if you are integrating with multiple competing vendors - the third-party vendors cannot see one another's integrations (or even know they exist).
If you give a third-party user access to an integration that uses custom components, you must also grant them access to those custom components.
Component access
Similar to integrations, you can grant third-party users access to specific custom components. By default, third-party users have access to Prismatic built-in public components, but you may not want third-party vendors to see all of the custom components you've published (especially if you integrate with several competing vendors).
To grant a third-party user access to a custom component, select Component after opening the + Add permission dialog, and then search for and select the component you would like to grant access to.
You can grant a variety of component-related permissions to a third-party user. If they are assisting in the development of the custom component, they will need the Edit Component permission. Otherwise, to use the component in an integration they will just need the View Component permission.
Custom components that are not granted to a user are not visible. This is once again handy if you are integrating with several competing companies, or your own competitors - their users will not be able to see what other custom components you've published.
Customer access
You can grant a third-party user access to a specific customer. This is handy if you and another vendor share a customer in common, and are working on an integration together for that customer.
To grant permissions to a specific customer, select Customer after clicking + PERMISSION and then select the customer you'd like to grant permissions for.
Next, select the permissions on this customer you would like to grant. There are a variety of options, each with a description below them. You can elect to let the third-party user view or manage the customer, the customer's users, and the instances deployed to the customer.
Note that if you grant the View Customer permission on a customer to a third-party user, that user can view the customer's saved credentials.
Permissions are scoped to a specific customer. That way, if you are developing an integration with a competing software vendor they will not be able to view information about the other customers in your system.